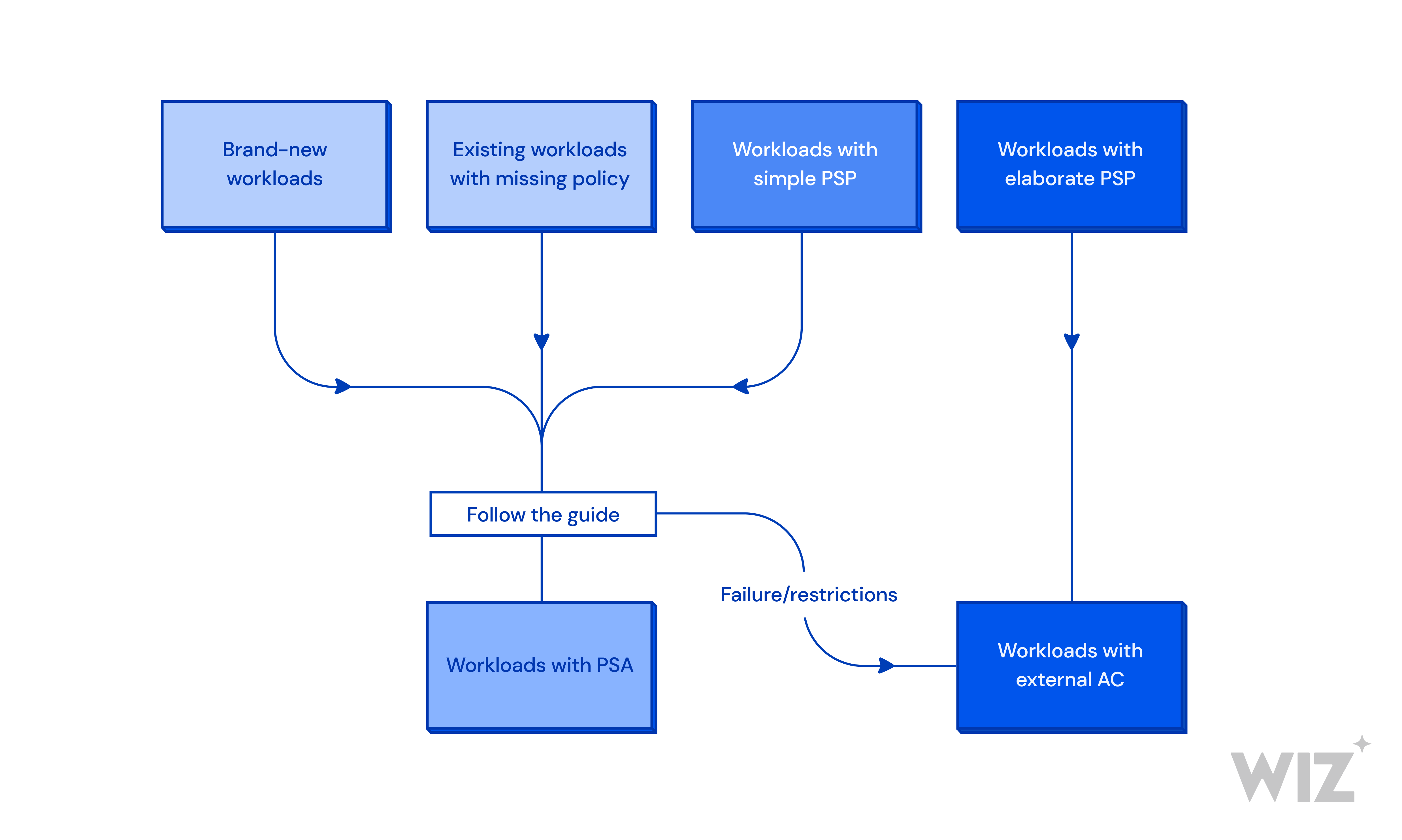
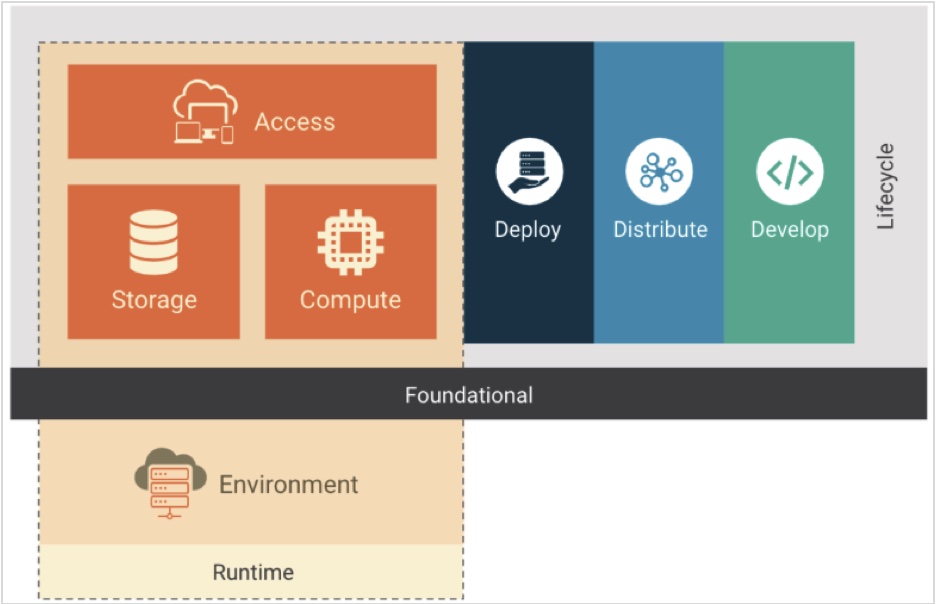
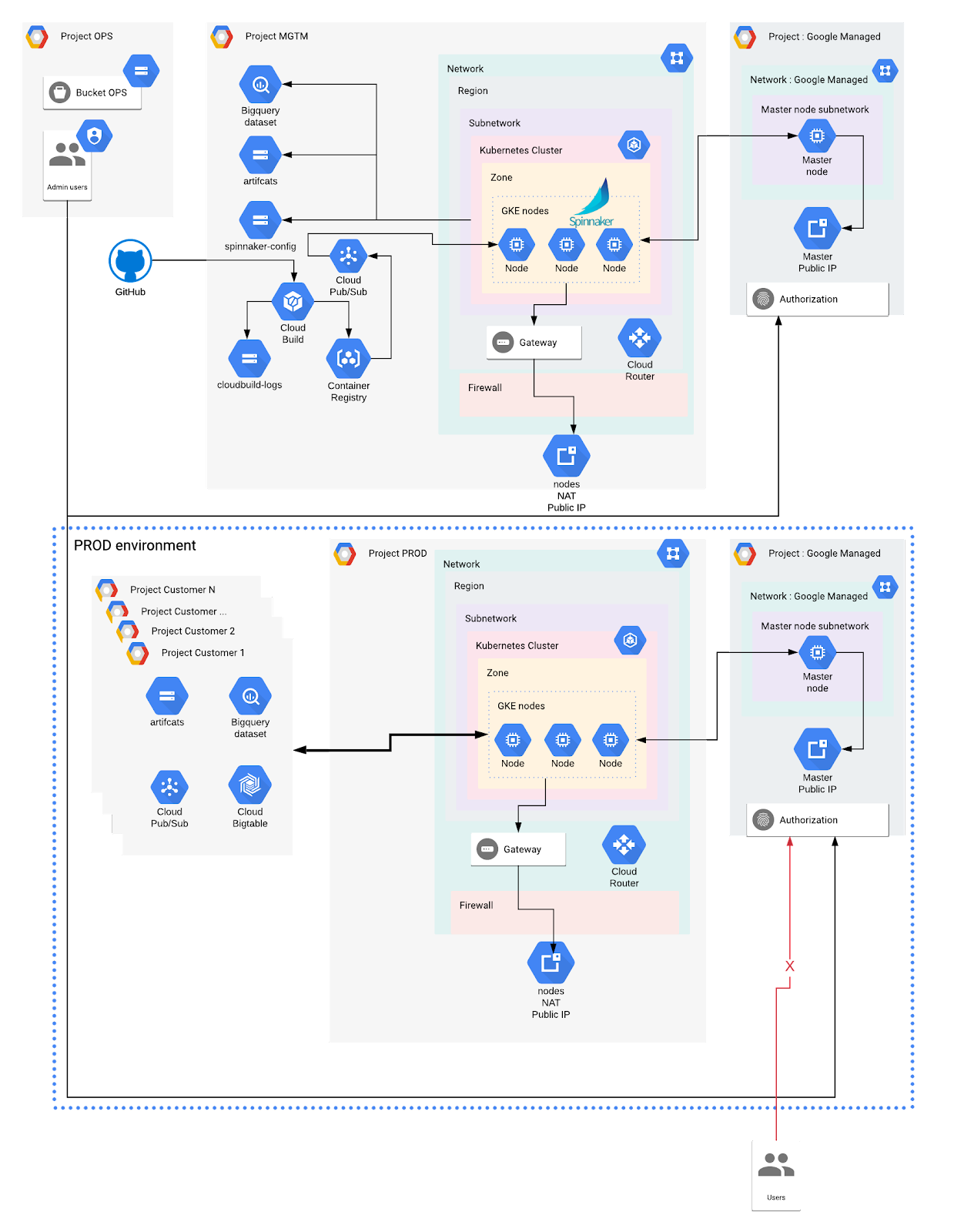
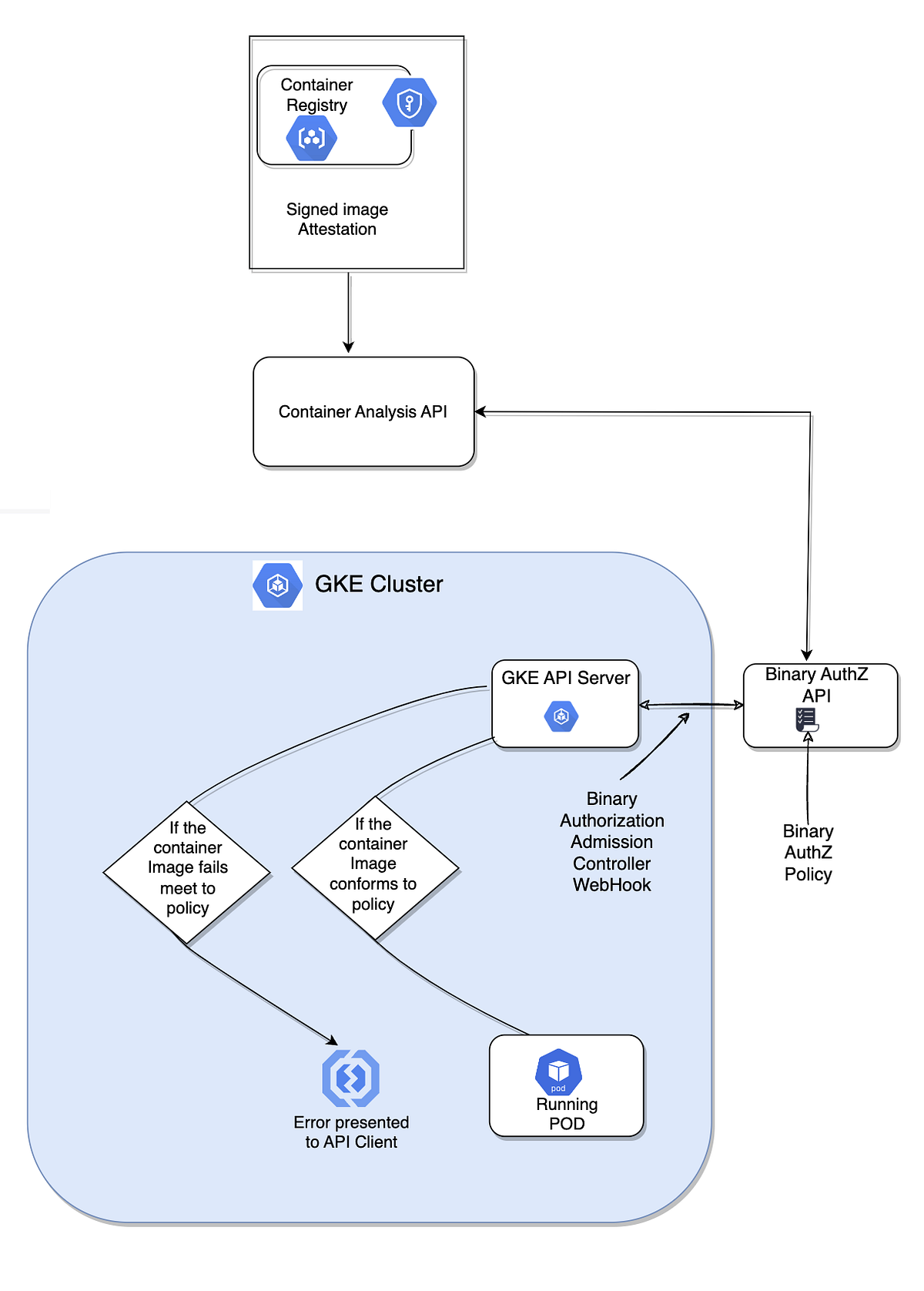
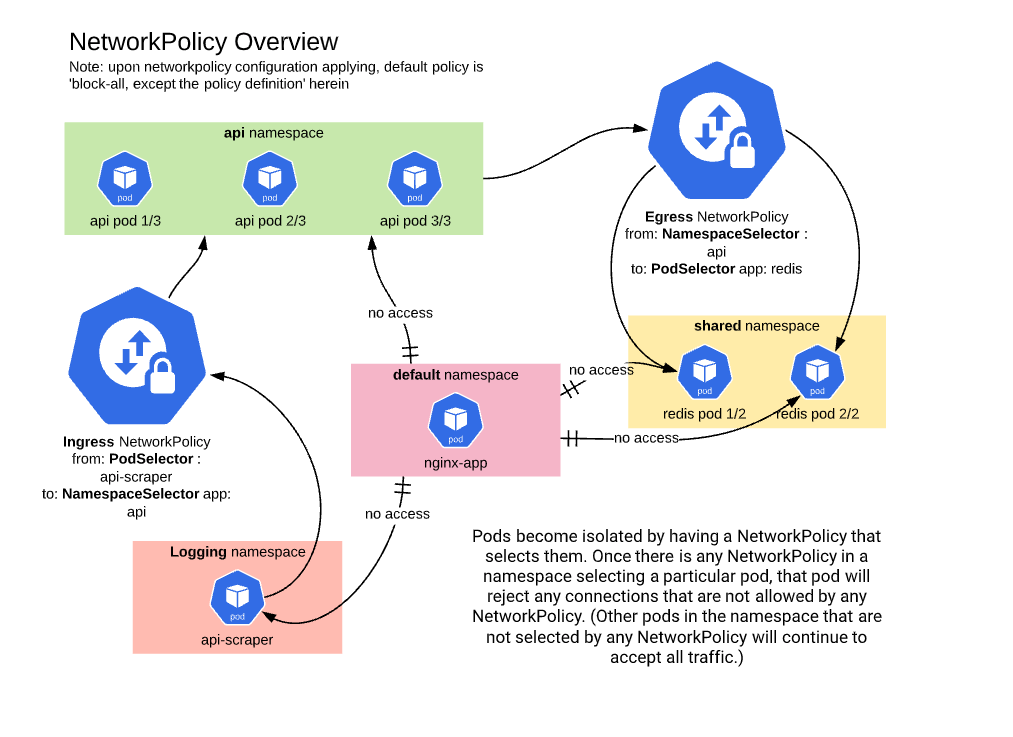
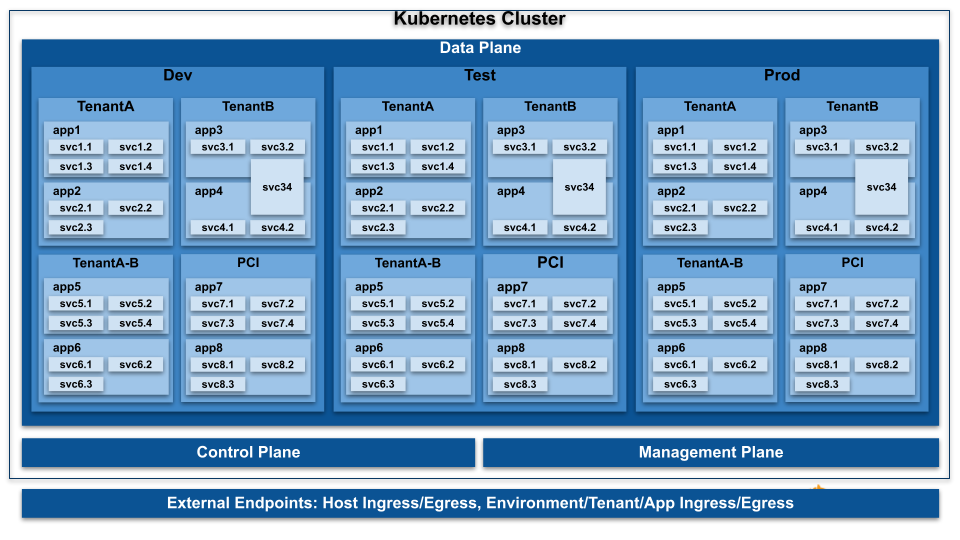
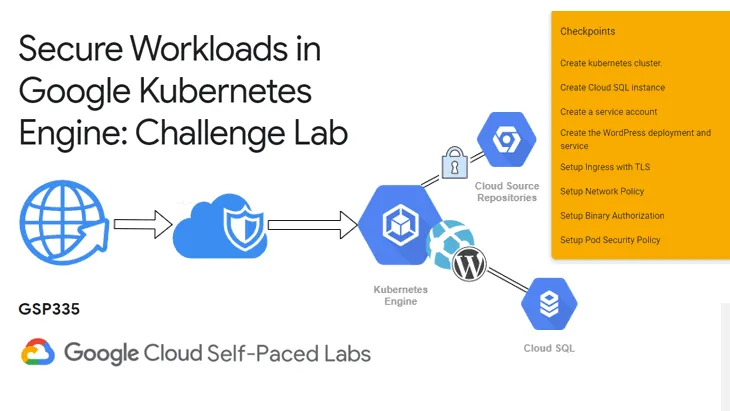
Designing a defense-in-depth network security model between Google Kubernetes Engine and Cloud SQL - DEV Community

Sécurité kubernetes : Comment réduire votre surface d'attaque grace à GKE : Anthos et policy controller | by Vincent Ledan | Medium