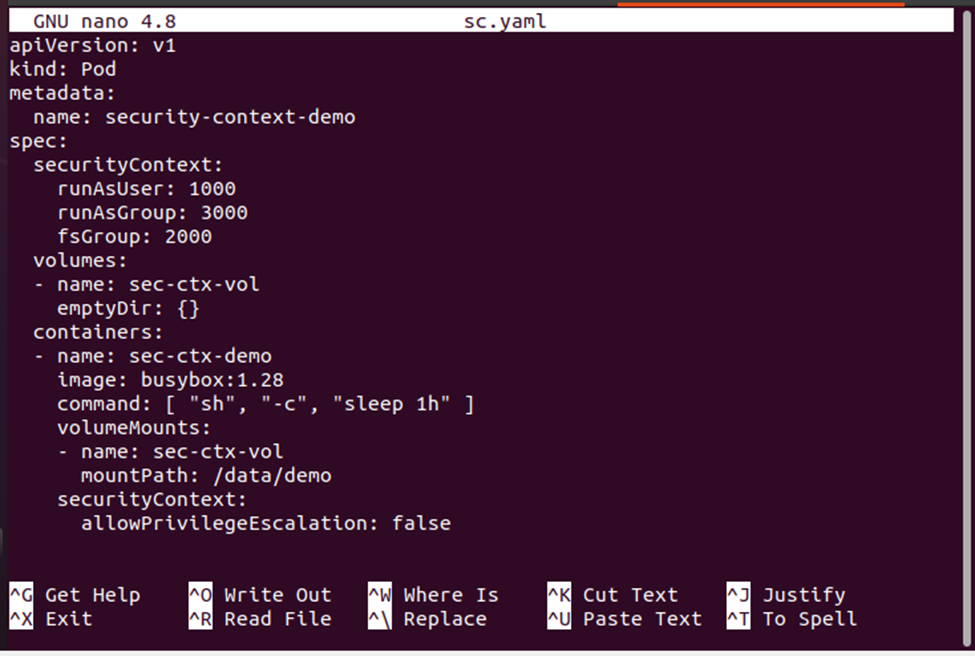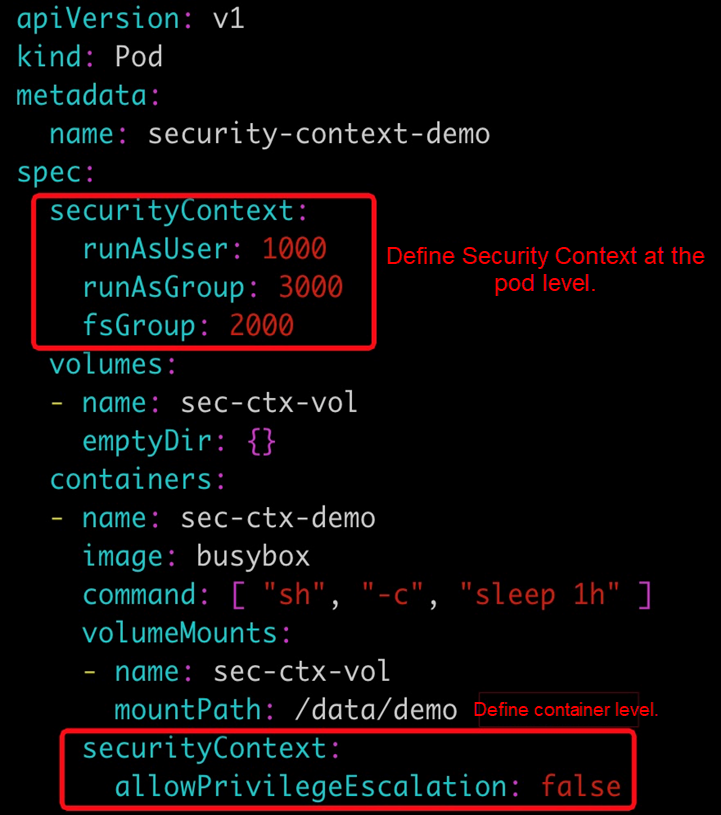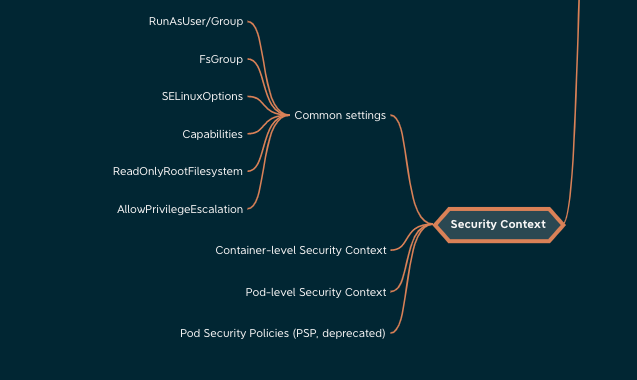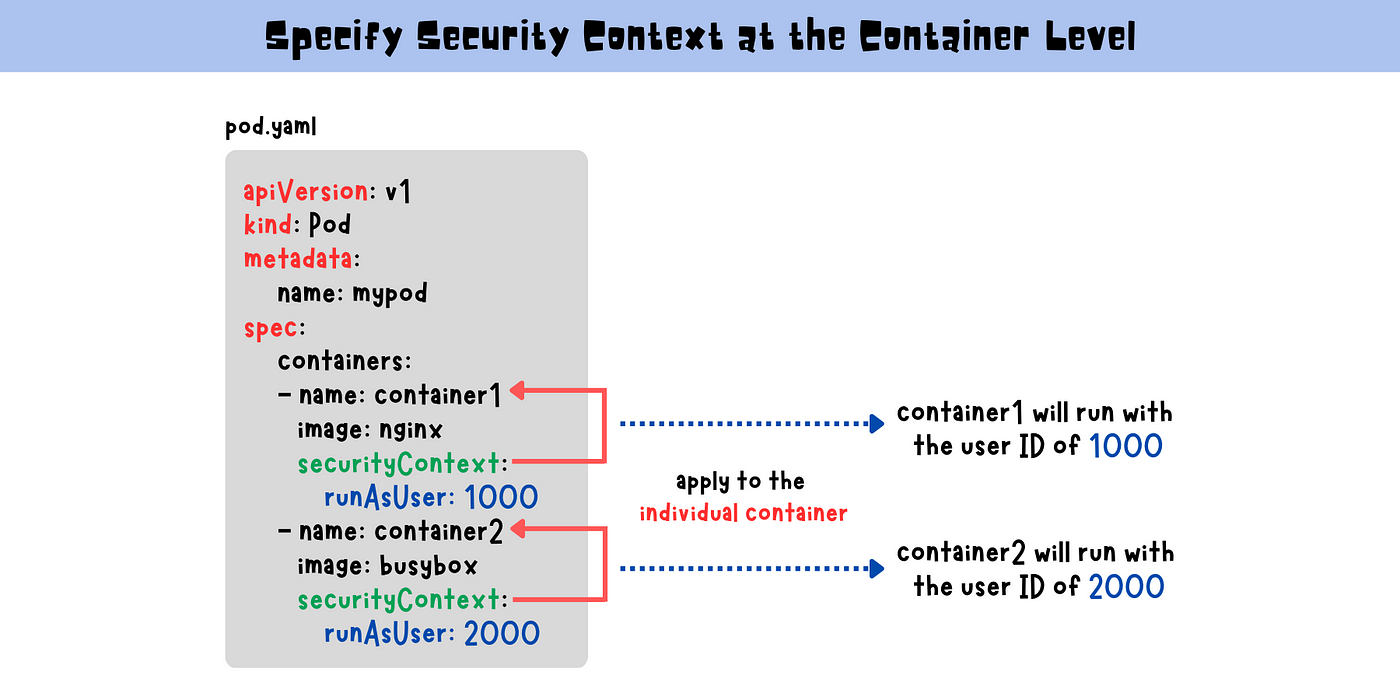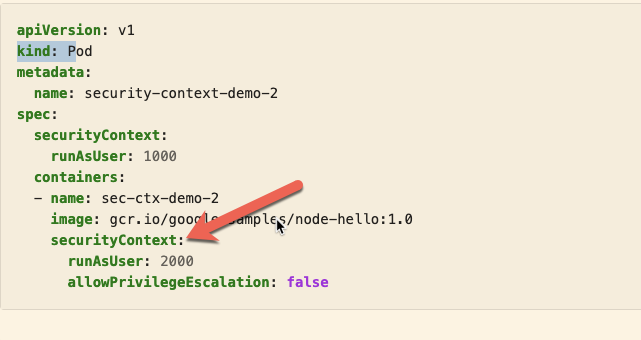
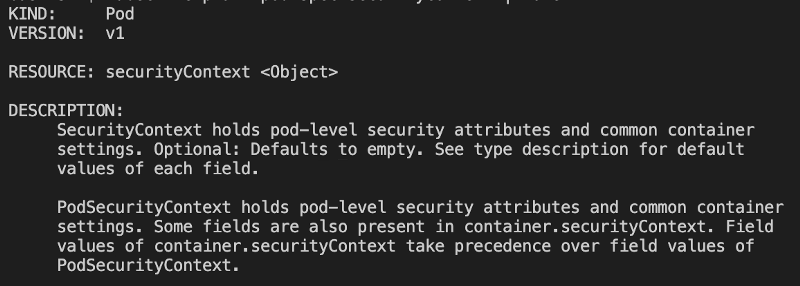
I saw that securityContext -> runAsUser can be applied both at the pod level . . . - Kubernetes - KodeKloud - DevOps Learning Community
Windows Pod with RunAsUserName and a Projected Volume does not honor file permissions in the volume · Issue #102849 · kubernetes/kubernetes · GitHub

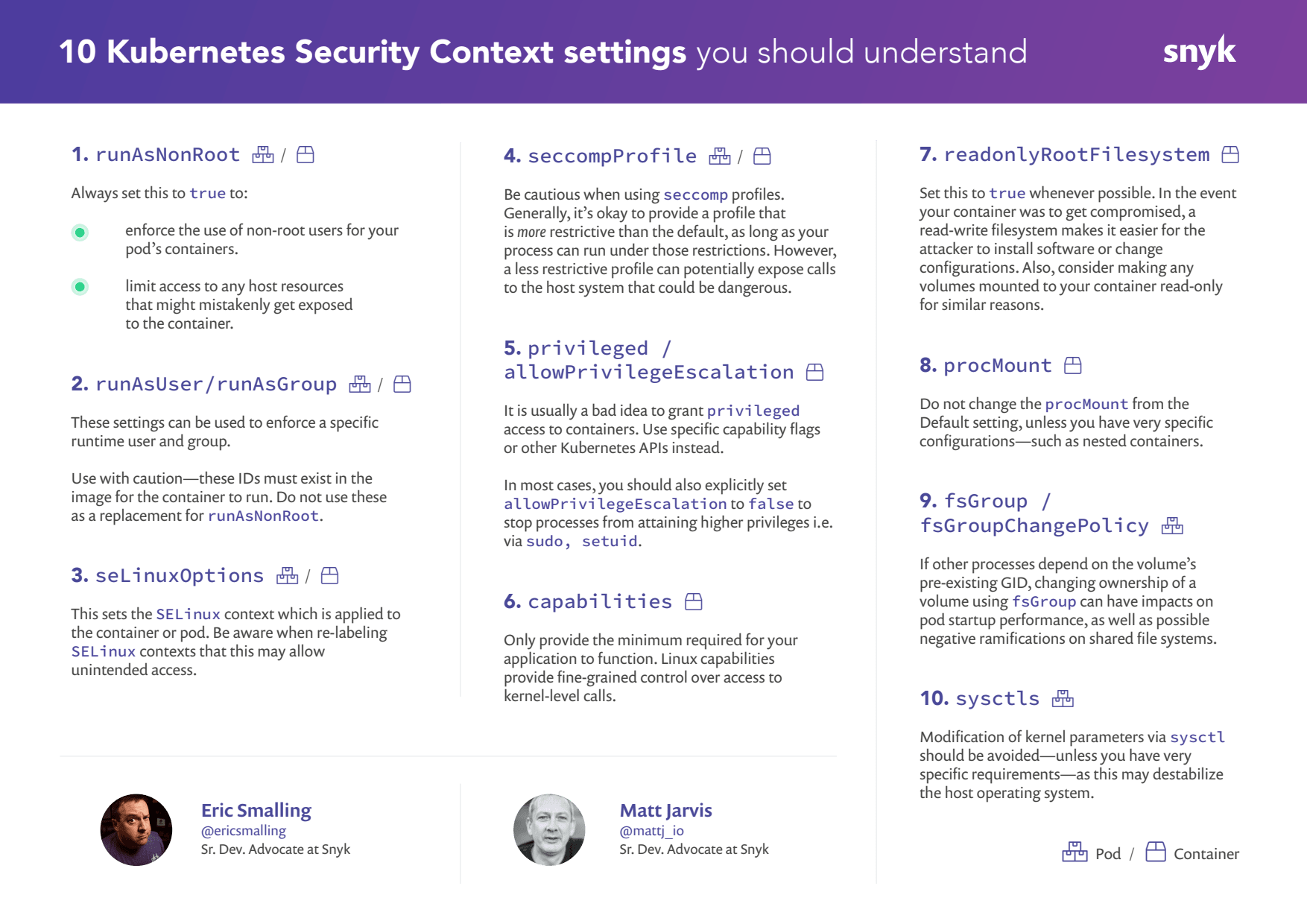
Sheila A. Berta on X: "Here I explain the configuration of Security Context and Policies in #Kubernetes 😁 it allows to define kernel capabilities, privileges, seccomp & apparmor profiles and more! ->
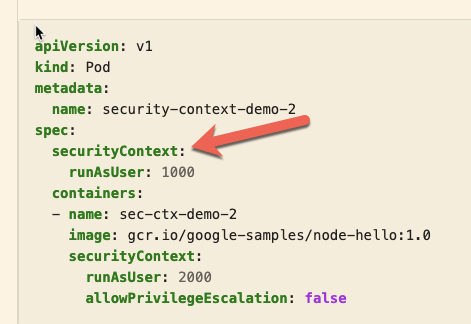
I saw that securityContext -> runAsUser can be applied both at the pod level . . . - Kubernetes - KodeKloud - DevOps Learning Community
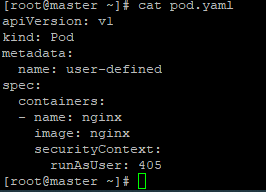
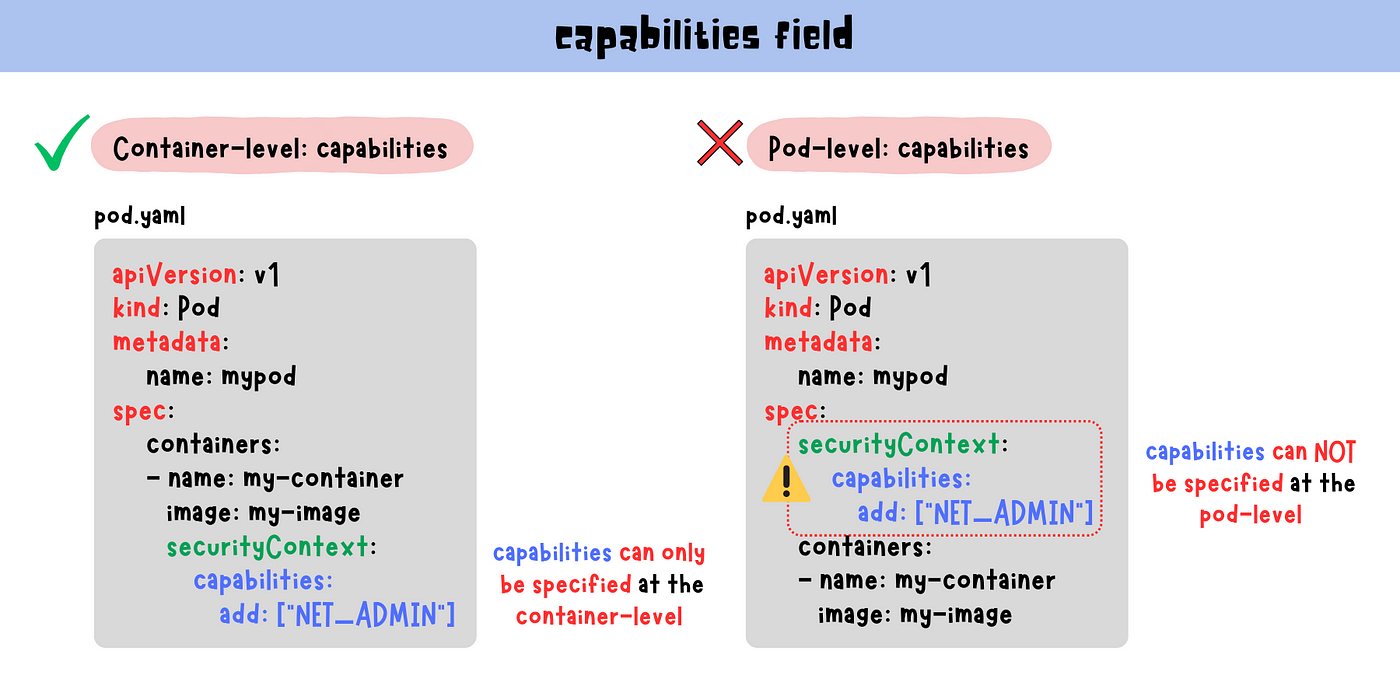
runAsUser and runAsGroup should cnsider Pod spec and not only container securityContext · Issue #126 · aquasecurity/appshield · GitHub





![4. Workload Runtime Security - Kubernetes Security and Observability [Book] 4. Workload Runtime Security - Kubernetes Security and Observability [Book]](https://www.oreilly.com/api/v2/epubs/9781098107093/files/assets/ksao_0401.png)