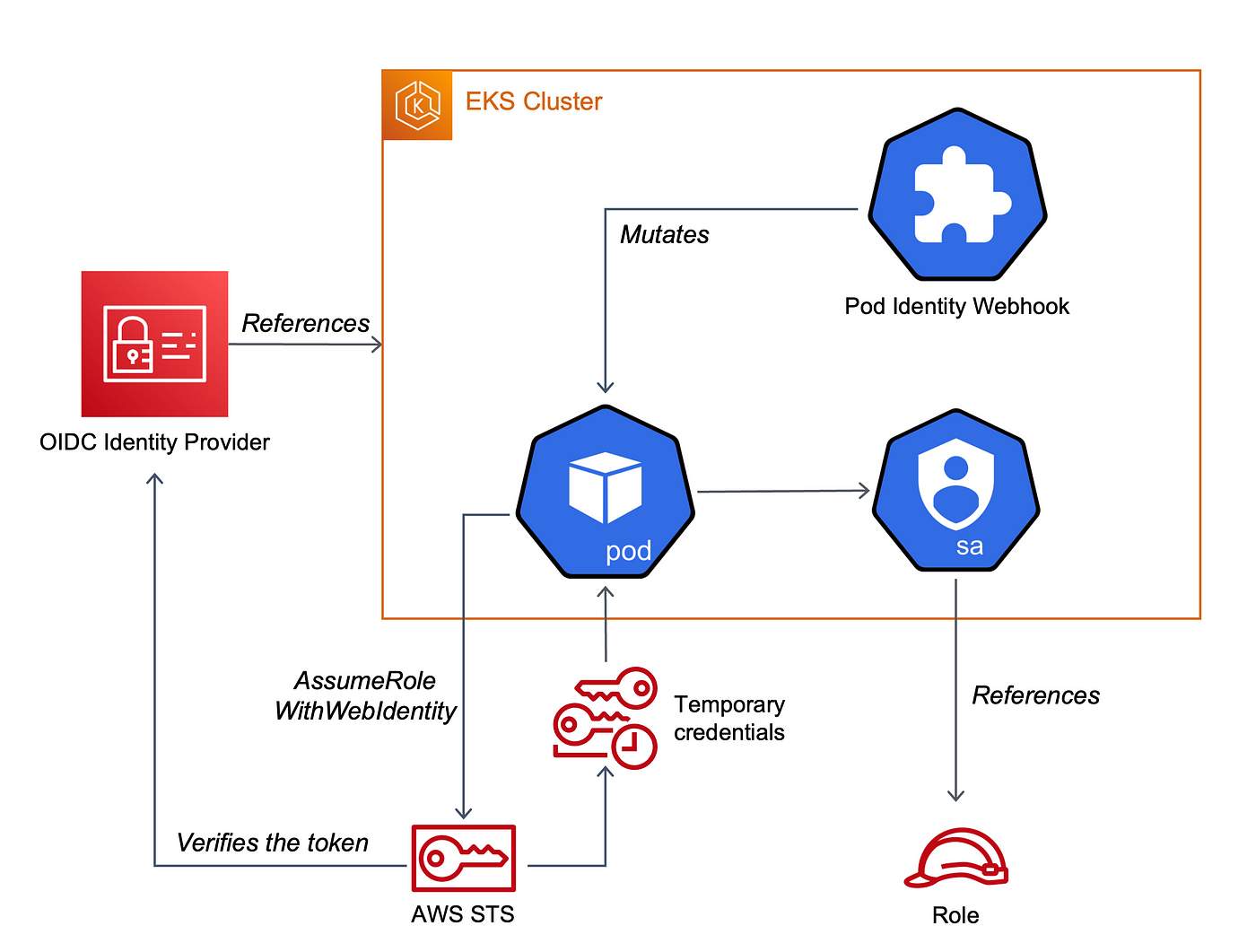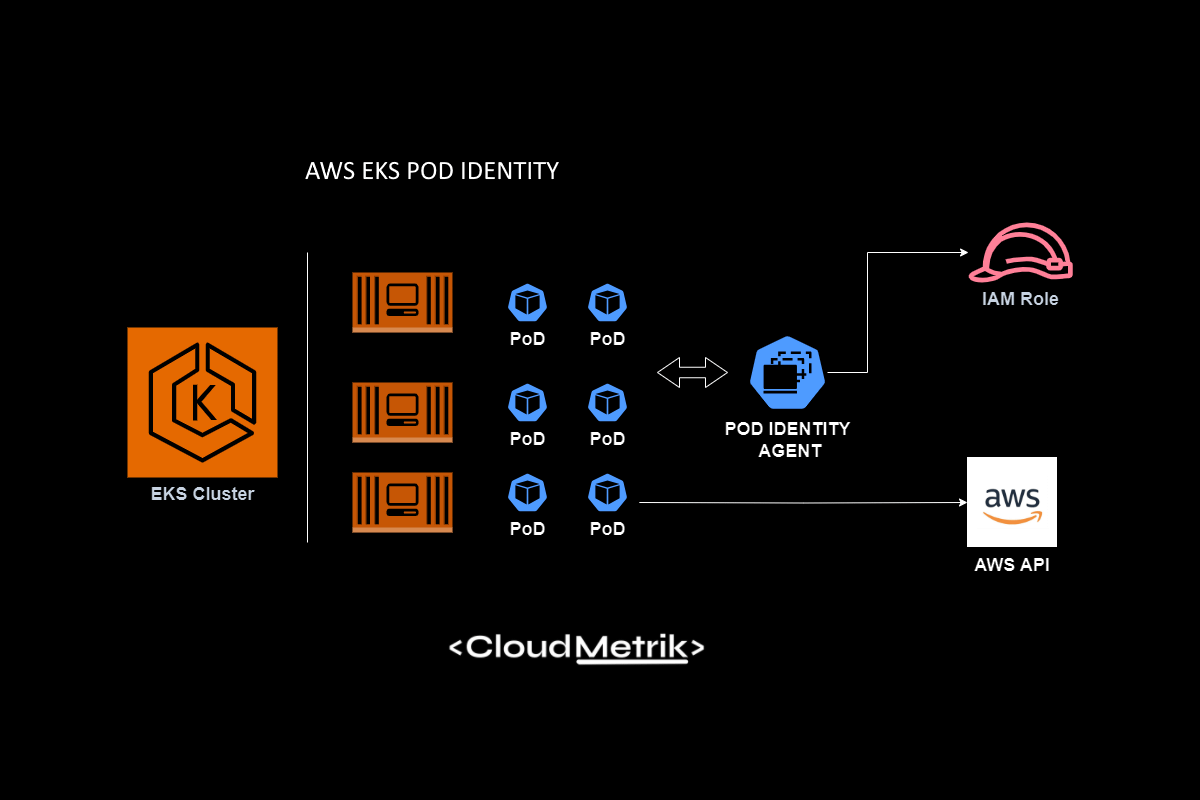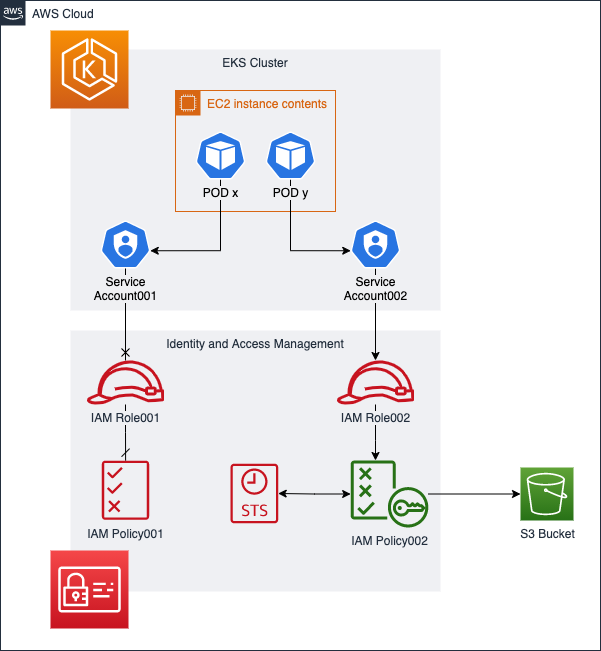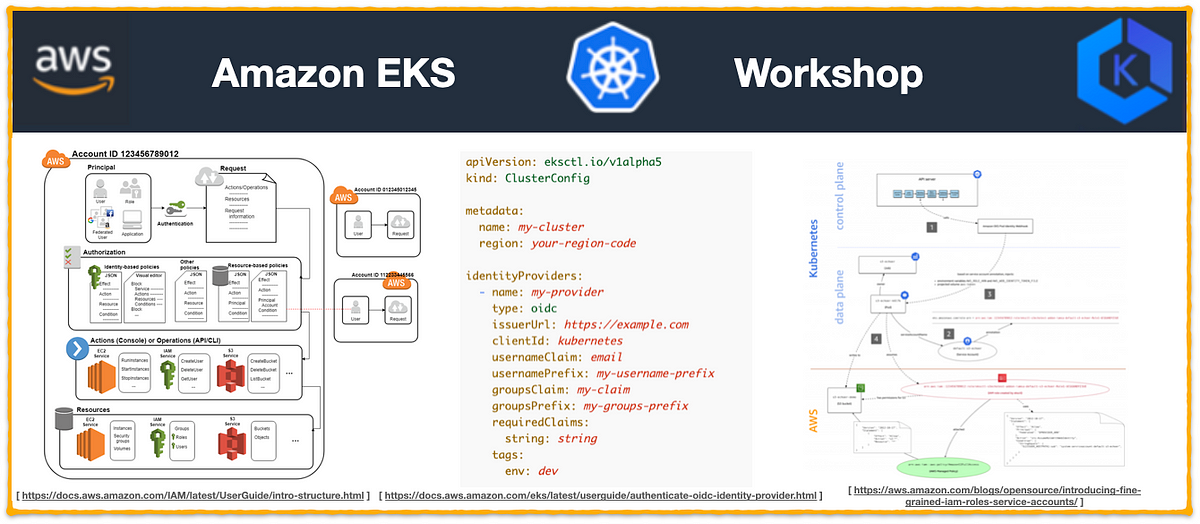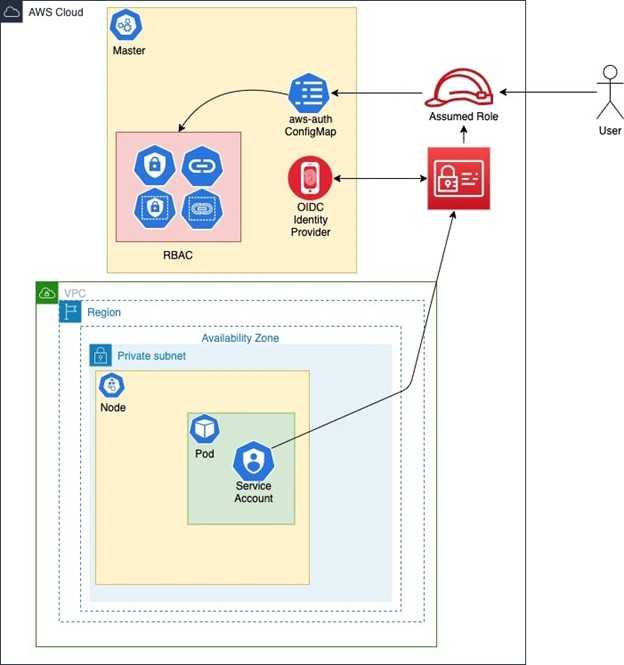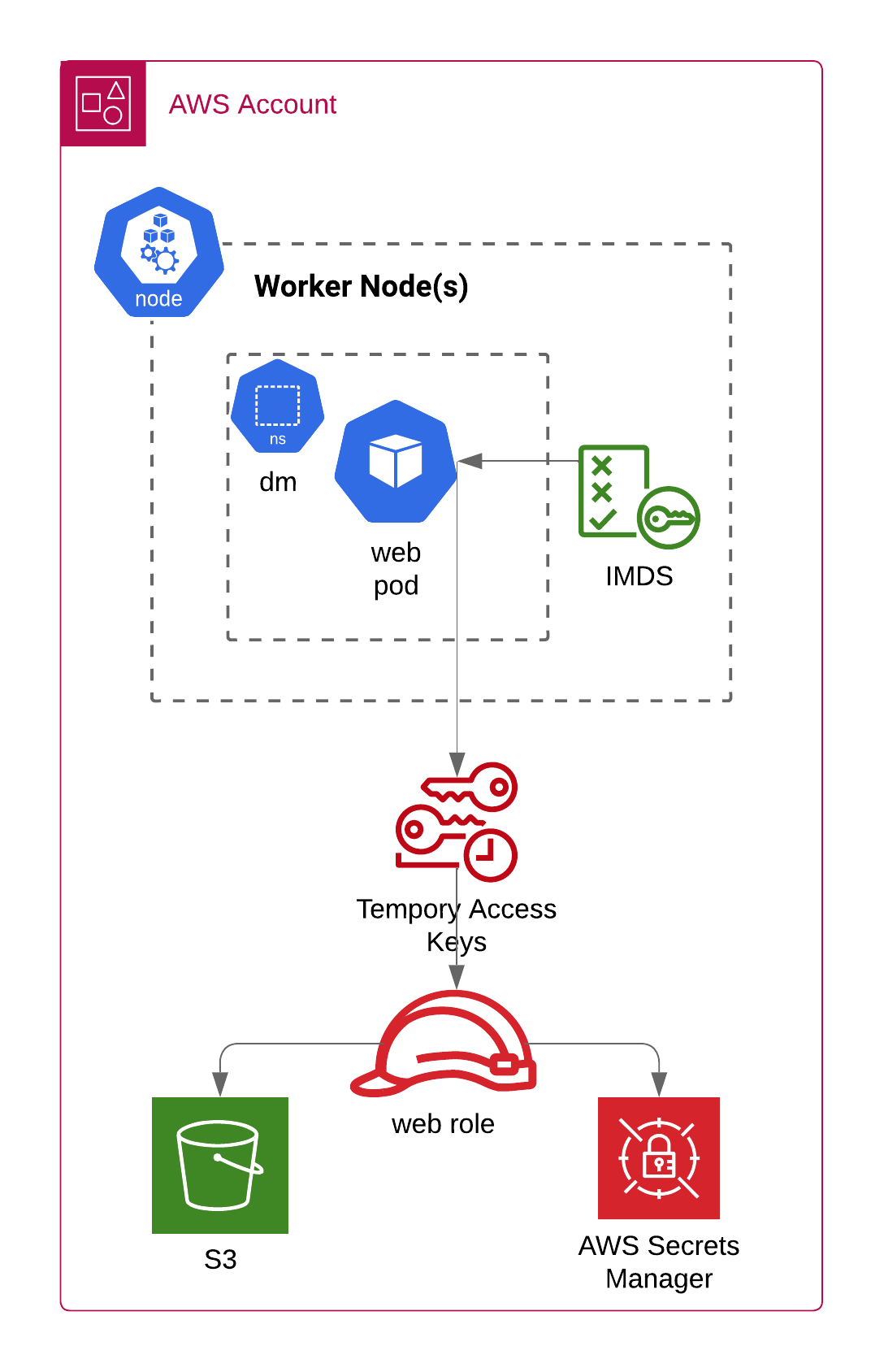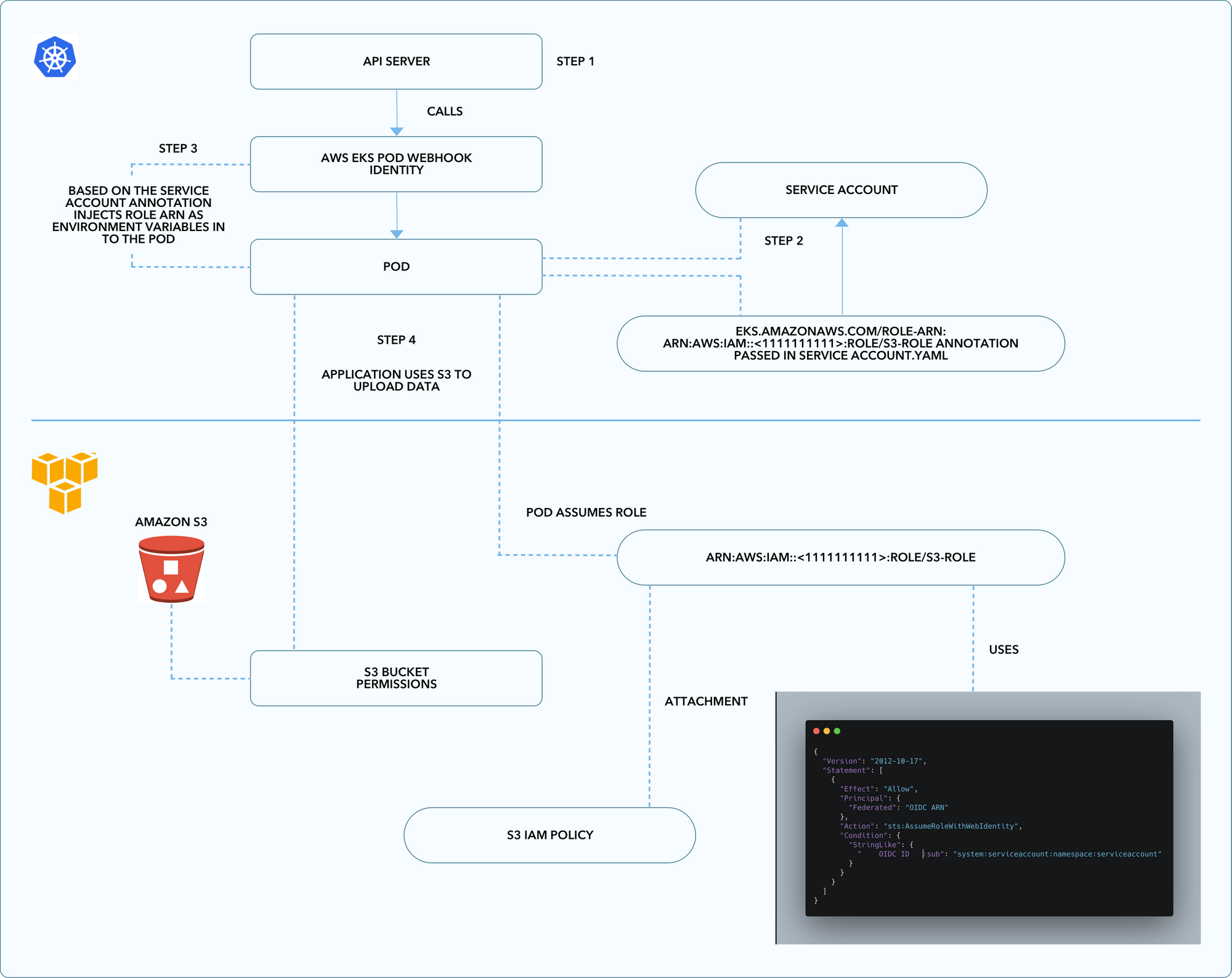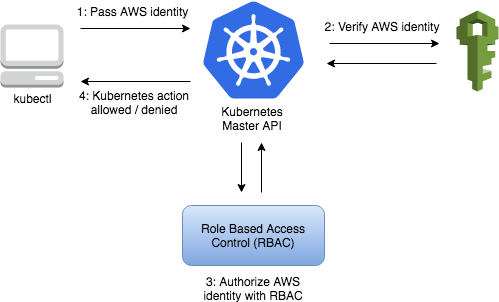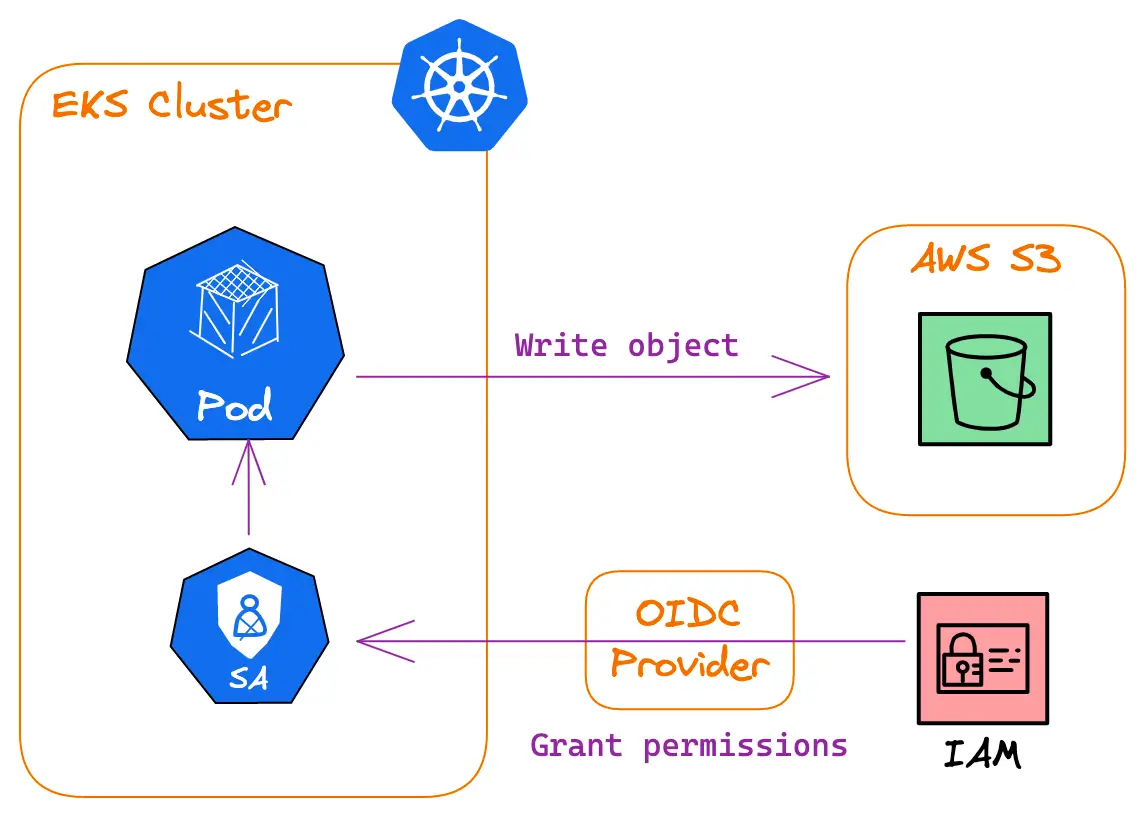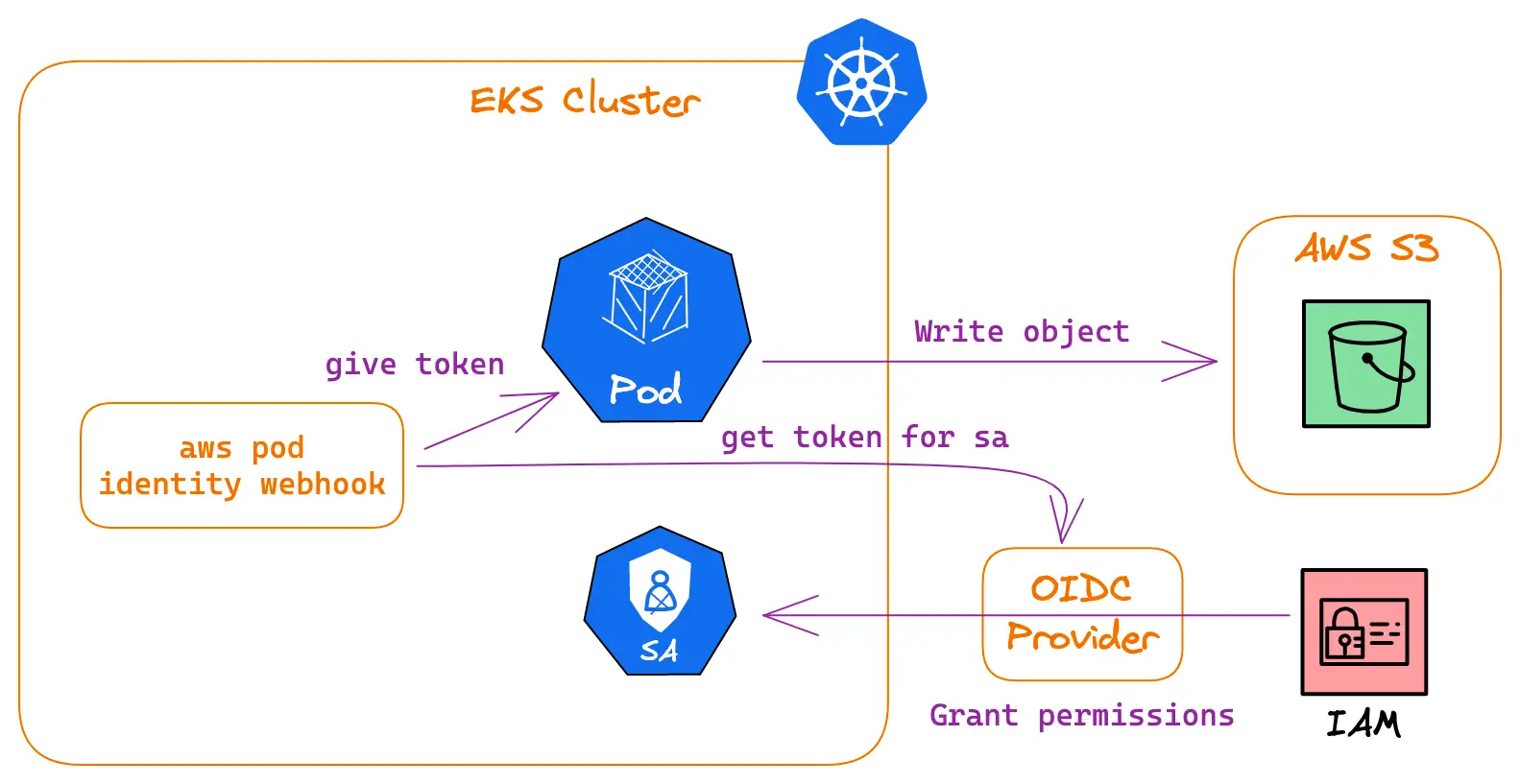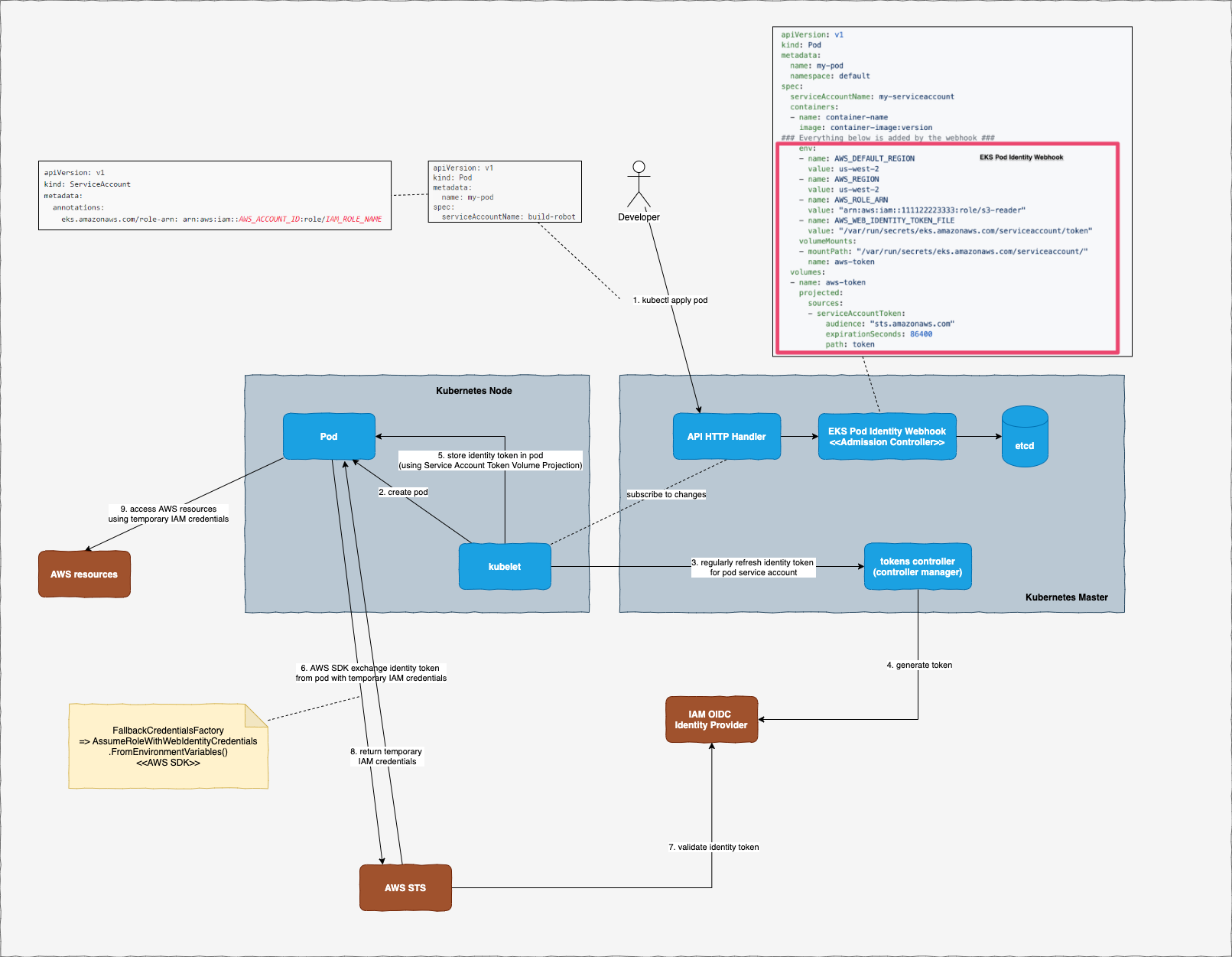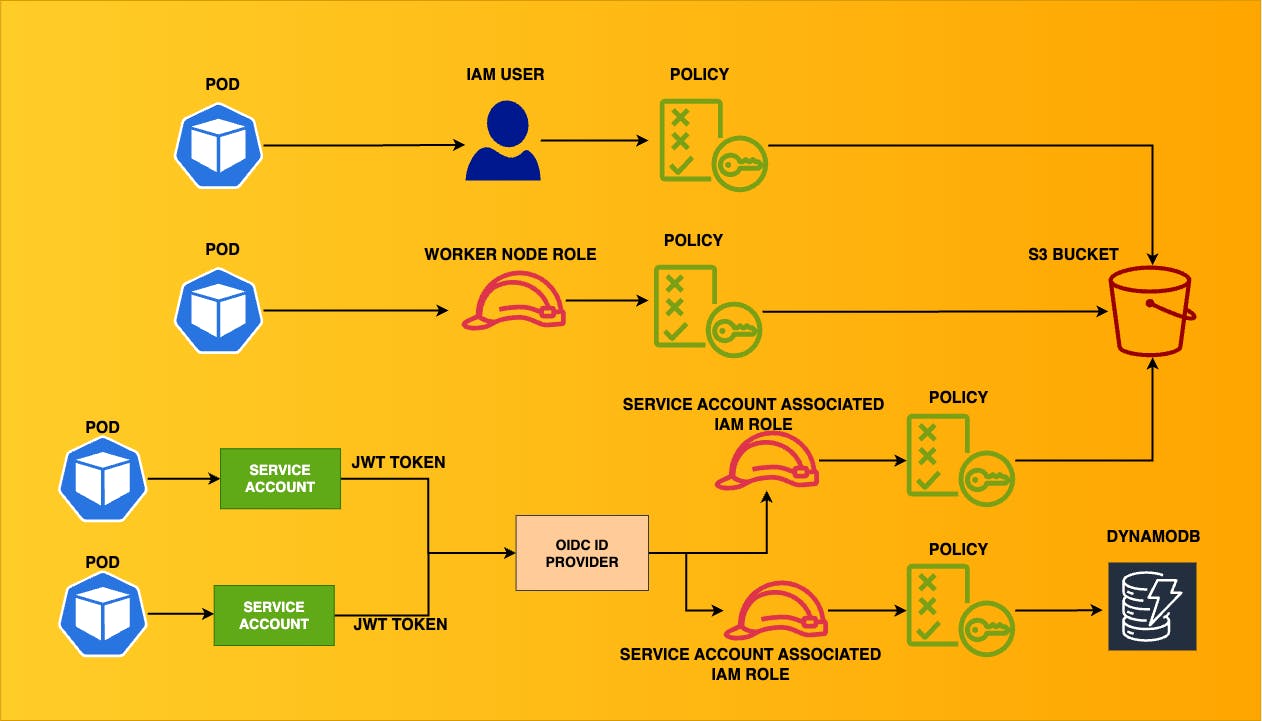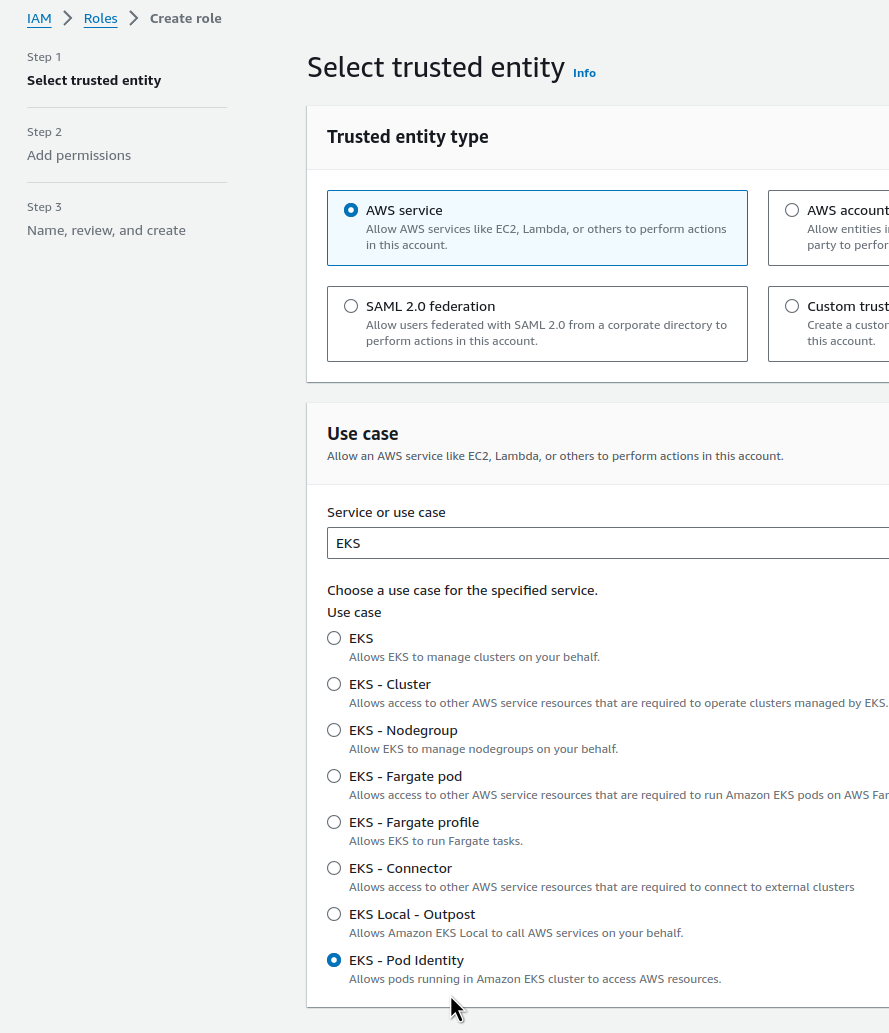
AWS: EKS Pod Identities — a replacement for IRSA? Simplifying IAM access management | by Arseny Zinchenko (setevoy) | ITNEXT

Combining IAM Roles for Service Accounts with Pod level Security Groups for a defense-in-depth strategy - DEV Community